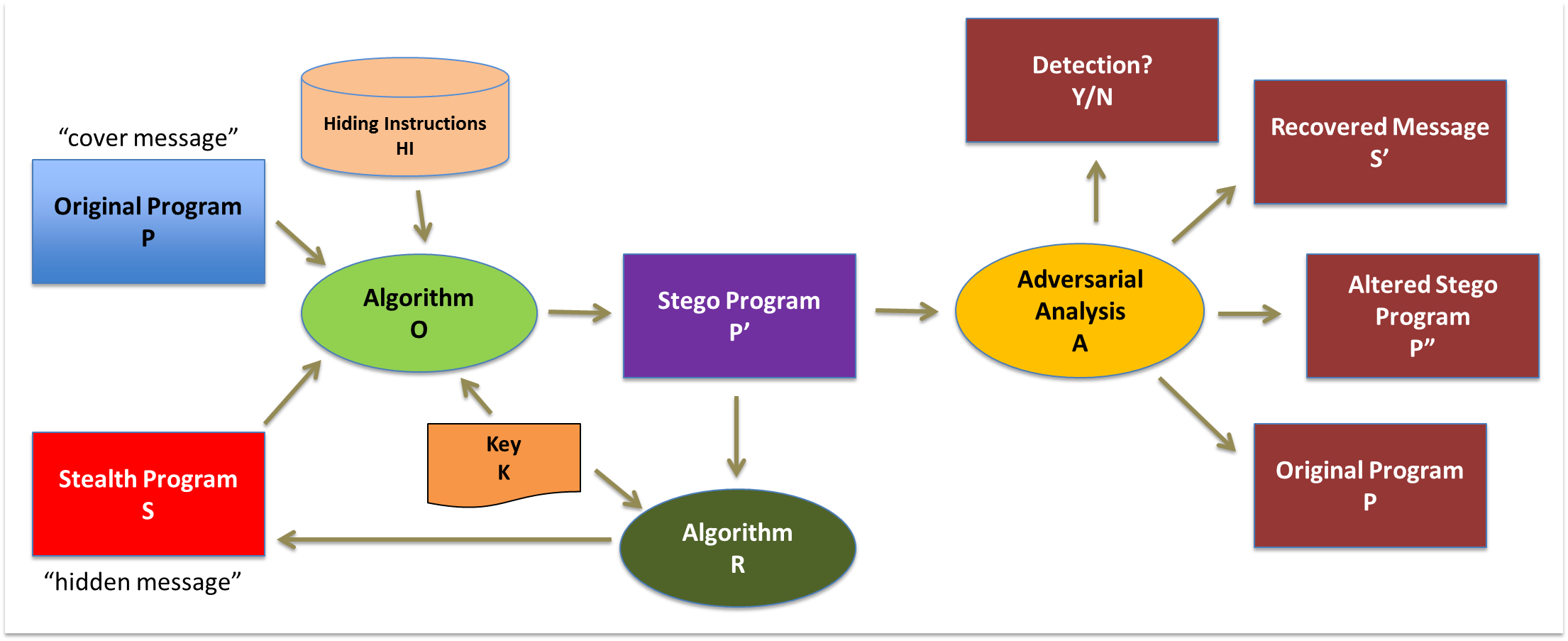
Hiding executable code within a target program so it is difficult to detect, remove, or alter through reverse engineering
Intellectual property protection of software remains a priority for the commercial sector because counterfeiting and piracy erode profits and market share, ultimately causing impacts on companies, consumers, and governments.
Watermarking (proving digital ownership) and obfuscation (hindering adversarial reverse engineering) is currently used to provide some level of deterrence against this. This project will investigate novel methods of software protection, hiding executable programs within other executable code.
Goals
Executable steganography is potentially an anti-reverse engineering technique and a way to watermark software. We aim to produce viable methods for hiding executable code, expand the state-of-the-art for this style of program protection, while also characterizing its effectiveness based on capacity, robustness, detectability, invisibility, and resilience.
Collaboration with the University of South Alabama
Both UNO and USA bring key opportunities for broader impacts of this research. Both have a rich tradition of meeting the needs of diverse student bodies, both are in EPSCoR states, with numerous students coming from rural areas. Both universities have extensive K-12 STEM outreach and Scholarship for Service students preparing for future cybersecurity careers. Our team can directly engage students in the research as part of their academic programs via course projects, senior capstone exercises, and labs.
Sponsor
This work is partially funded by National Science Foundation awards 1811560 and 1811578 in the NSF 17-576 Secure and Trustworthy Cyberspace (SaTC) program.